Edited by Marilyn Outerbridge
Editor’s note: This is the latest in a series of blog posts of NAT configuration. Click below for previous installments:
Table of Contents
The NAT examples in the article are taken from the following topology:
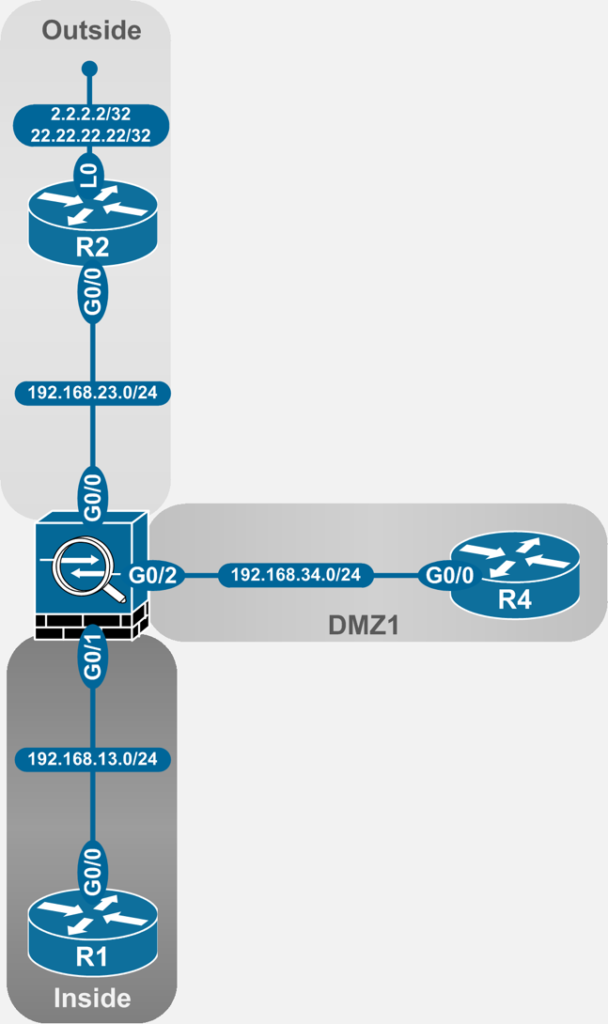
Dynamic NAT
As opposed to dynamic PAT which was essentially dynamic NAT with overload, dynamic NAT features no overload functionality in its most basic form. Each global IP address is mapped to a single local IP address, thus, as the packet passes thru the ASA, the port fields are left untouched and only the IP addresses are translated. This has very important consequences for matching traffic.
For the most basic form of dynamic NAT, the total number of simultaneous internal IP hosts that can use the pool is equal to the number of global IPs in the pool.
It must be noted, however, that the translation is still dynamic. It is created on demand when a matching packet traverses the ASA. There is also a finite timeout associated with the mapping which allows the translation to be deleted from the NAT translation table.
What this means from an operation point of view is that a dynamic NAT translation is still uni-directional. E.g. a dynamic NAT rule cannot be used to expose an internal/DMZ server to the internet.
Dynamic NAT without Fallback
This is the most basic form of dynamic NAT. As noted earlier, this form of dynamic NAT will support translations for a finite number of internal hosts. Specifically, the number of internal hosts supported will be equal to the number of global IPs available in the dynamic NAT pool.
Once again, there are two options (technically three with Manual NAT After-Auto) available to the ASA administrator.
Using Network Object NAT (NON)
Unique Pool Per Interface
For this scenario, the ASA is translating the inside IP block, 192.168.11.0/24 to the following pools:
- 192.168.33.60 – 192.168.33.65 on interface outside
- 192.168.33.50 – 192.168.33.55 on interface dmz1
The block 192.168.11.0 has been implemented as /32 loopback interfaces on R1:
R1#sho ip int b | in Loop
Loopback1 192.168.11.1 YES manual up up
Loopback2 192.168.11.2 YES manual up up
Loopback3 192.168.11.3 YES manual up up
Loopback4 192.168.11.4 YES manual up up
Loopback5 192.168.11.5 YES manual up up
Loopback6 192.168.11.6 YES manual up up
Loopback7 192.168.11.7 YES manual up up
Loopback8 192.168.11.8 YES manual up up
Loopback9 192.168.11.9 YES manual up up
Loopback10 192.168.11.10 YES manual up up
To start the demo on a “fresh” ASA, all existing NAT configuration as well as the objects were deleted:
ASA1(config)# clear configure nat
ASA1(config)# clear configure object
ASA1(config)# sho run nat
ASA1(config)# sho run object
ASA1(config)#
Two new objects are created to hold the global IP address pools.
ASA1(config)# object network obj_192.168.33.50-55
ASA1(config-network-object)# range 192.168.33.50 192.168.33.55
ASA1(config-network-object)# object network obj_192.168.33.60-65
ASA1(config-network-object)# range 192.168.33.60 192.168.33.65
Another two new objects are created to hold the internal IP addresses being translated, one each for the two global interfaces, outside and dmz1. Inside these new objects, NAT statements are configured to enable dynamic NAT.
ASA1(config)# object network obj_192.168.11.0_outside
ASA1(config-network-object)# subnet 192.168.11.0 255.255.255.0
ASA1(config-network-object)# nat (inside,outside) dynamic obj_192.168.33.60-65
ASA1(config-network-object)# exit
ASA1(config)# object network obj_192.168.11.0_dmz
ASA1(config-network-object)# subnet 192.168.11.0 255.255.255.0
ASA1(config-network-object)# nat (inside,outside) dynamic obj_192.168.33.50-55
ASA1(config-network-object)# exit
As noted in earlier posts, the ASA stores these pieces of configuration at different places in the running-configuration.
ASA1(config)# sho run object
<SNIP>
object network obj_192.168.11.0_outside
subnet 192.168.11.0 255.255.255.0
object network obj_192.168.11.0_dmz
subnet 192.168.11.0 255.255.255.0
ASA1(config)#
ASA1(config)# sho run nat
!
object network obj_192.168.11.0_outside
nat (inside,outside) dynamic obj_192.168.33.60-65
object network obj_192.168.11.0_dmz
nat (inside,outside) dynamic obj_192.168.33.50-55
For those keen minds who are comparing this configuration to the similar looking configuration in part 3 of the series, the major difference is the lack of the pat-pool knob. That knob essentially made the dynamic NAT definitions “overloaded” in the last post.
The key point here is that there are six mapped IPs available in each pool. Because the NAT pool is not overloaded, this means only six internal IPs can use the pool before it is exhausted.
To verify this, 12 simultaneous connections are launched from R1. Each telnet session is launched from a different loopback interface, Loopback 1 to Loopback 6. Of these, six are telnet connections to R2 and six to R4.
Verification on Source
R1#sho tcp brief | in 23.2
0CE387C8 192.168.11.6.48615 192.168.23.2.23 ESTAB
0CE39458 192.168.11.5.64804 192.168.23.2.23 ESTAB
0CE37B38 192.168.11.4.29330 192.168.23.2.23 ESTAB
0D16CF30 192.168.11.1.25414 192.168.23.2.23 ESTAB
0CE36EA8 192.168.11.3.36078 192.168.23.2.23 ESTAB
0CD2AE58 192.168.11.2.59861 192.168.23.2.23 ESTAB
R1#sho tcp brief | in 34.4
0CD39540 192.168.11.4.26463 192.168.34.4.23 ESTAB
0CD3AE60 192.168.11.6.55150 192.168.34.4.23 ESTAB
0B9ABE00 192.168.11.3.30324 192.168.34.4.23 ESTAB
0CD3A1D0 192.168.11.5.62275 192.168.34.4.23 ESTAB
0D260BC8 192.168.11.1.30745 192.168.34.4.23 ESTAB
0B9AAB60 192.168.11.2.51240 192.168.34.4.23 ESTAB
R1#
Verification on Destinations
R2#sho tcp brief
TCB Local Address Foreign Address (state)
0BAED2E8 192.168.23.2.23 192.168.33.63.64804 ESTAB
0A1ED538 192.168.23.2.23 192.168.33.64.25414 ESTAB
0D2CC510 192.168.23.2.23 192.168.33.60.36078 ESTAB
0BAEA900 192.168.23.2.23 192.168.33.62.48615 ESTAB
0CD2C100 192.168.23.2.23 192.168.33.61.59861 ESTAB
0BAE8070 192.168.23.2.23 192.168.33.65.29330 ESTAB
!
R4#sho tcp brief
TCB Local Address Foreign Address (state)
0BAF9550 192.168.34.4.23 192.168.33.55.62275 ESTAB
0D16B9F0 192.168.34.4.23 192.168.33.51.30745 ESTAB
0BAF69B0 192.168.34.4.23 192.168.33.54.26463 ESTAB
0CD2D4F8 192.168.34.4.23 192.168.33.53.30324 ESTAB
0BAFBC60 192.168.34.4.23 192.168.33.50.55150 ESTAB
0CD2BFA0 192.168.34.4.23 192.168.33.52.51240 ESTAB
It is apparent on comparison that:
- Translations are taking place
- The translations are one-to-one in nature – i.e. each internal IP is mapped to a unique global IP
Next verification steps are on the ASA.
The first verification is to inspect the Xlate table:
ASA1(config)# sho xlate
12 in use, 12 most used
Flags: D - DNS, e - extended, I - identity, i - dynamic, r - portmap,
s - static, T - twice, N - net-to-net
NAT from inside:192.168.11.5 to dmz1:192.168.33.55 flags i idle 0:02:54 timeout 3:00:00
NAT from inside:192.168.11.5 to outside:192.168.33.63 flags i idle 0:03:40 timeout 3:00:00
NAT from inside:192.168.11.1 to outside:192.168.33.64 flags i idle 0:03:59 timeout 3:00:00
NAT from inside:192.168.11.1 to dmz1:192.168.33.51 flags i idle 0:04:34 timeout 3:00:00
NAT from inside:192.168.11.3 to dmz1:192.168.33.53 flags i idle 0:03:01 timeout 3:00:00
NAT from inside:192.168.11.3 to outside:192.168.33.60 flags i idle 0:03:48 timeout 3:00:00
NAT from inside:192.168.11.6 to dmz1:192.168.33.50 flags i idle 0:02:52 timeout 3:00:00
NAT from inside:192.168.11.6 to outside:192.168.33.62 flags i idle 0:03:44 timeout 3:00:00
NAT from inside:192.168.11.2 to dmz1:192.168.33.52 flags i idle 0:03:05 timeout 3:00:00
NAT from inside:192.168.11.2 to outside:192.168.33.61 flags i idle 0:03:51 timeout 3:00:00
NAT from inside:192.168.11.4 to dmz1:192.168.33.54 flags i idle 0:02:57 timeout 3:00:00
NAT from inside:192.168.11.4 to outside:192.168.33.65 flags i idle 0:03:46 timeout 3:00:00
Thus, the translations are one-to-one as verified earlier on sources and destinations.
Next, the state of the respective pools and their usage.
ASA1# sho nat pool
NAT pool outside:obj_192.168.33.60-65, range 192.168.33.60-192.168.33.65, allocated 6
NAT pool dmz1:obj_192.168.33.50-55, range 192.168.33.50-192.168.33.55, allocated 6
The ASA confirms that it has allocated all six of the IPs available in each pool. This essentially means that there are no more IPs left in the pool to hand out, i.e. the pool has reached exhaustion.
This can be verified by launching one more TCP connection from R1 to both R2 and R4 with a new, unique IP.
R1#telnet 192.168.23.2 /source-interface l7
Trying 192.168.23.2 ...
% Connection timed out; remote host not responding
R1#telnet 192.168.34.4 /source-interface l7
Trying 192.168.34.4 ...
% Connection timed out; remote host not responding
R1#
As expected, the connections did not complete. But was it really due to NAT pool exhaustion?
ASA1# sho logg | in NAT
%ASA-3-202010: NAT pool exhausted. Unable to create TCP connection from inside:192.168.11.7/14306 to outside:192.168.23.2/23
%ASA-3-202010: NAT pool exhausted. Unable to create TCP connection from inside:192.168.11.7/14306 to outside:192.168.23.2/23
%ASA-3-202010: NAT pool exhausted. Unable to create TCP connection from inside:192.168.11.7/14306 to outside:192.168.23.2/23
%ASA-3-202010: NAT pool exhausted. Unable to create TCP connection from inside:192.168.11.7/14306 to outside:192.168.23.2/23
%ASA-3-202010: NAT pool exhausted. Unable to create TCP connection from inside:192.168.11.7/65302 to dmz1:192.168.34.4/23
%ASA-3-202010: NAT pool exhausted. Unable to create TCP connection from inside:192.168.11.7/65302 to dmz1:192.168.34.4/23
%ASA-3-202010: NAT pool exhausted. Unable to create TCP connection from inside:192.168.11.7/65302 to dmz1:192.168.34.4/23
%ASA-3-202010: NAT pool exhausted. Unable to create TCP connection from inside:192.168.11.7/65302 to dmz1:192.168.34.4/23
Thus, it is clear that the pools are definitely exhausted.
Sharing a Pool Amongst Interfaces
This scenario is similar to the above scenario with one key difference. A new pool of 6 addresses is defined and is shared amongst the outside and dmz1 interfaces. The previous NAT configuration is removed (while keeping the objects intact). In its place, the new NAT configuration refers to the newly created global IP pool for both outside and dmz1 objects. Here is the effective configuration on the ASA:
ASA1(config)# clear configure nat
ASA1(config)# object network obj_192.168.33.70-75_any
ASA1(config-network-object)# range 192.168.33.70 192.168.33.75
ASA1(config-network-object)# exit
ASA1(config)#
ASA1(config)# object network obj_192.168.11.0_outside
ASA1(config-network-object)# nat (inside,outside) dynamic obj_192.168.33.70-75_any
ASA1(config-network-object)# exit
ASA1(config)# object network obj_192.168.11.0_dmz
ASA1(config-network-object)# nat (inside,dmz1) dynamic obj_192.168.33.70-75_any
ASA1(config-network-object)# exit
The major difference here is the apparent size of this pool. It is still true that the pool has six total addresses but because it is being used for multiple interfaces, it essentially means that there are six mapped addresses available per interface, i.e. a total of 12 internal IPs can be translated.
Verification on Source
R1#sho tcp brief | in 23.2
0B435618 192.168.11.1.51661 192.168.23.2.23 ESTAB
0CD39C40 192.168.11.5.61309 192.168.23.2.23 ESTAB
0D16CF30 192.168.11.2.14082 192.168.23.2.23 ESTAB
0CD38FB0 192.168.11.4.44430 192.168.23.2.23 ESTAB
0CD3A8D0 192.168.11.6.53818 192.168.23.2.23 ESTAB
0CE35860 192.168.11.3.51260 192.168.23.2.23 ESTAB
R1#sho tcp brief | in 34.4
0B9AA040 192.168.11.7.35524 192.168.34.4.23 ESTAB
0B9ABF70 192.168.11.9.17465 192.168.34.4.23 ESTAB
0CE37438 192.168.11.10.25426 192.168.34.4.23 ESTAB
0B9AACD0 192.168.11.8.11995 192.168.34.4.23 ESTAB
Verification on Destinations
R2#sho tcp brief | in ESTAB
0D32B4A0 192.168.23.2.23 192.168.33.75.61309 ESTAB
0CD2AED8 192.168.23.2.23 192.168.33.73.51661 ESTAB
0BAEF4E0 192.168.23.2.23 192.168.33.71.51260 ESTAB
0BAECB90 192.168.23.2.23 192.168.33.72.14082 ESTAB
09F33AF8 192.168.23.2.23 192.168.33.74.53818 ESTAB
0D371288 192.168.23.2.23 192.168.33.70.44430 ESTAB
!
R4#sho tcp brief
TCB Local Address Foreign Address (state)
0BAF7418 192.168.34.4.23 192.168.33.74.25426 ESTAB
0BAF4B20 192.168.34.4.23 192.168.33.73.17465 ESTAB
0D2B9D40 192.168.34.4.23 192.168.33.75.35524 ESTAB
0CD2CB90 192.168.34.4.23 192.168.33.72.11995 ESTAB
That proves that IPs 72-75 are being used to translate different internal IPs. This becomes a little clearer when verified on the ASA.
ASA1# sho xlate
10 in use, 12 most used
Flags: D - DNS, e - extended, I - identity, i - dynamic, r - portmap,
s - static, T - twice, N - net-to-net
NAT from inside: 192.168.11.5 to outside:192.168.33.75 flags i idle 0:06:34 timeout 3:00:00
NAT from inside: 192.168.11.7 to dmz1:192.168.33.75 flags i idle 0:06:22 timeout 3:00:00
NAT from inside:192.168.11.1 to outside:192.168.33.73 flags i idle 0:06:48 timeout 3:00:00
NAT from inside:192.168.11.3 to outside:192.168.33.71 flags i idle 0:06:40 timeout 3:00:00
NAT from inside:192.168.11.8 to dmz1:192.168.33.72 flags i idle 0:06:17 timeout 3:00:00
NAT from inside:192.168.11.6 to outside:192.168.33.74 flags i idle 0:06:31 timeout 3:00:00
NAT from inside:192.168.11.2 to outside:192.168.33.72 flags i idle 0:06:43 timeout 3:00:00
NAT from inside:192.168.11.10 to dmz1:192.168.33.74 flags i idle 0:06:10 timeout 3:00:00
NAT from inside:192.168.11.4 to outside:192.168.33.70 flags i idle 0:06:37 timeout 3:00:00
NAT from inside:192.168.11.9 to dmz1:192.168.33.73 flags i idle 0:06:13 timeout 3:00:00
The reason for this is that the ASA has created two pools, one per unique interface from the same parent object obj_192.168.33.70-75_any. This provides a sum total of 12 IPs across two interfaces, 6 on each.
ASA1# sho nat pool
NAT pool outside:obj_192.168.33.70-75_any, range 192.168.33.70-192.168.33.75, allocated 6
NAT pool dmz1:obj_192.168.33.70-75_any, range 192.168.33.70-192.168.33.75, allocated 4
As a last demo to drive the point home, pool outside: obj_192.168.33.70-75 has still reached exhaustion because the maximum limit of six has been reached for connections to R2. Thus, R1 cannot launch another connection to R2 with a new, unique source IP.
Verification on R1
R1#telnet 192.168.23.2 /source-interface l7
Trying 192.168.23.2 ...
% Connection timed out; remote host not responding
R1#
Pool exhaustion verification on the ASA:
ASA1# sho logg | in NAT
%ASA-3-202010: NAT pool exhausted. Unable to create TCP connection from inside:192.168.11.7/35305 to outside:192.168.23.2/23
%ASA-3-202010: NAT pool exhausted. Unable to create TCP connection from inside:192.168.11.7/35305 to outside:192.168.23.2/23
%ASA-3-202010: NAT pool exhausted. Unable to create TCP connection from inside:192.168.11.7/35305 to outside:192.168.23.2/23
%ASA-3-202010: NAT pool exhausted. Unable to create TCP connection from inside:192.168.11.7/35305 to outside:192.168.23.2/23
Using Manual NAT
The concepts discussed under NON are applicable, as usual, directly under Manual NAT. The blog post will list the syntax for all the examples above using Manual NAT but not the detailed verifications for the sake of brevity.
Unique Pool per Interface
object network obj_192.168.33.50-55
range 192.168.33.50 192.168.33.55
object network obj_192.168.33.60-65
range 192.168.33.60 192.168.33.65
!
object network obj_192.168.11.0_outside
subnet 192.168.11.0 255.255.255.0
object network obj_192.168.11.0_dmz
subnet 192.168.11.0 255.255.255.0
!
nat (inside,outside) source dynamic obj_192.168.11.0_outside obj_192.168.33.60-65
nat (inside,dmz1) source dynamic obj_192.168.11.0_dmz obj_192.168.33.50-55
Sharing a Pool Amongst Interfaces
object network obj_192.168.11.0_outside
subnet 192.168.11.0 255.255.255.0
object network obj_192.168.11.0_dmz
subnet 192.168.11.0 255.255.255.0
object network obj_192.168.33.70-75_any
range 192.168.33.70 192.168.33.75
!
nat (inside,outside) source dynamic obj_192.168.11.0_outside obj_192.168.33.70-75_any
nat (inside,dmz1) source dynamic obj_192.168.11.0_dmz obj_192.168.33.70-75_any
Dynamic NAT with Fallback IP
Since NAT pool exhaustion is a common issue, there are options available to use a single IP as a “fallback” IP. What this means is that when the pool is exhausted, this IP is used for dynamic PAT (NAT overload) for any further IPs requiring translation. There are two main ways of declaring this IP.
Using Network Object NAT
Configuring a Specific Fallback IP
In the first case, a specific IP is chosen for PAT services and is configured manually. The configuration is a little different than those seen before as this configuration uses an object-group instead of an object for the translation.
This object-group contains two things:
- An object that defines the dynamic NAT range
- The fallback IP defined either as an object or as a host
All previous NAT configuration is removed. It should be noted that the demonstration is performed only for inside-to-outside translation.
To demonstrate this behavior, the following range and fallback IP is used:
- Dynamic NAT – 192.168.33.70-75
- Fallback PAT IP – 192.168.33.76
The configuration of the object-group would take one of the following forms:
Object Configuration
ASA1(config)# sho run object id obj_192.168.33.70-75_any
object network obj_192.168.33.70-75_any
range 192.168.33.70 192.168.33.75
ASA1(config)# object network obj_192.168.33.76_fallback
ASA1(config-network-object)# host 192.168.33.76
ASA1(config-network-object)# exit
Object-group Configuration with Object as Fallback IP
ASA1(config)# object-group network OG_NAT_Fallback
ASA1(config-network-object-group)# network-object object obj_192.168.33.70-75_any
ASA1(config-network-object-group)# network-object object obj_192.168.33.76_fallback
Alternative Object-group Configuration with Manual Fallback IP
ASA1(config-network-object-group)# network-object object obj_192.168.33.70-75_any
ASA1(config-network-object-group)# network-object host 192.168.33.76
In the specific example used for the demonstration, the former configuration, i.e. fallback IP in an object, is being used.
The next step is the same as before with the only change being the use of an object-group in the NAT statement as opposed to an object.
ASA1(config)# clear configure nat
ASA1(config)# sho run object-group
object-group network OG_NAT_Fallback
network-object object obj_192.168.33.70-75_any
network-object object obj_192.168.33.76_fallback
ASA1(config)# object network obj_192.168.11.0_outside
ASA1(config-network-object)# nat (inside,outside) dynamic OG_NAT_Fallback
ASA1(config-network-object)# exit
For verification, the same six TCP connections are created between R1 and R2.
Verification on Source
R1#sho tcp brief
TCB Local Address Foreign Address (state)
0CD38FB0 192.168.11.2.40459 192.168.23.2.23 ESTAB
0B435618 192.168.11.1.51286 192.168.23.2.23 ESTAB
0CD3A340 192.168.11.5.59937 192.168.23.2.23 ESTAB
0CD2AE58 192.168.11.6.46220 192.168.23.2.23 ESTAB
0CD396B0 192.168.11.4.13563 192.168.23.2.23 ESTAB
0D16C6C8 192.168.11.3.51104 192.168.23.2.23 ESTAB
Verification on Destination
R2#sho tcp brief
TCB Local Address Foreign Address (state)
0D3134C8 192.168.23.2.23 192.168.33.70.46220 ESTAB
0D16CD20 192.168.23.2.23 192.168.33.72.51286 ESTAB
0CD2C428 192.168.23.2.23 192.168.33.74.51104 ESTAB
0BAEC180 192.168.23.2.23 192.168.33.71.13563 ESTAB
0D2B7668 192.168.23.2.23 192.168.33.73.40459 ESTAB
0BAE7CA8 192.168.23.2.23 192.168.33.75.59937 ESTAB
On the ASA, it can be verified that the translation as dynamic NAT as opposed to PAT as well as the dynamic NAT pool has been exhausted.
ASA1(config)# sho xlate
6 in use, 12 most used
Flags: D - DNS, e - extended, I - identity, i - dynamic, r - portmap,
s - static, T - twice, N - net-to-net
NAT from inside:192.168.11.5 to outside:192.168.33.75 flags i idle 0:02:24 timeout 3:00:00
NAT from inside:192.168.11.1 to outside:192.168.33.72 flags i idle 0:02:36 timeout 3:00:00
NAT from inside:192.168.11.3 to outside:192.168.33.74 flags i idle 0:02:31 timeout 3:00:00
NAT from inside:192.168.11.6 to outside:192.168.33.70 flags i idle 0:02:21 timeout 3:00:00
NAT from inside:192.168.11.2 to outside:192.168.33.73 flags i idle 0:02:33 timeout 3:00:00
NAT from inside:192.168.11.4 to outside:192.168.33.71 flags i idle 0:02:27 timeout 3:00:00
ASA1(config)#
ASA1(config)# sho nat pool
NAT pool outside:obj_192.168.33.70-75_any, range 192.168.33.70-192.168.33.75, allocated 6
ASA1(config)#
But the fallback address is not visible yet. That is essentially because the ASA has not needed it so far. If more unique internal IPs now match that same NAT rule, the ASA will have to use the fallback IP as a dynamic PAT IP.
To verify this scenario, three more connections, with unique IPs are launched from R1.
R1#telnet 192.168.23.2 /source-interface l7
Trying 192.168.23.2 ... Open
R2>
R1#telnet 192.168.23.2 /source-interface l8
Trying 192.168.23.2 ... Open
R2>
R1#telnet 192.168.23.2 /source-interface l9
Trying 192.168.23.2 ... Open
R2>
All three connections succeed. The ASA can now be used for verification of the nature of the three new connections.
ASA1(config)# sho xlate
9 in use, 12 most used
Flags: D - DNS, e - extended, I - identity, i - dynamic, r - portmap,
s - static, T - twice, N - net-to-net
NAT from inside:192.168.11.5 to outside:192.168.33.75 flags i idle 0:07:04 timeout 3:00:00
TCP PAT from inside:192.168.11.7/41235 to outside:192.168.33.76/41235 flags ri idle 0:01:14 timeout 0:00:30
NAT from inside:192.168.11.1 to outside:192.168.33.72 flags i idle 0:07:16 timeout 3:00:00
NAT from inside:192.168.11.3 to outside:192.168.33.74 flags i idle 0:07:11 timeout 3:00:00
TCP PAT from inside:192.168.11.8/17762 to outside:192.168.33.76/17762 flags ri idle 0:01:10 timeout 0:00:30
NAT from inside:192.168.11.6 to outside:192.168.33.70 flags i idle 0:07:01 timeout 3:00:00
NAT from inside:192.168.11.2 to outside:192.168.33.73 flags i idle 0:07:13 timeout 3:00:00
NAT from inside:192.168.11.4 to outside:192.168.33.71 flags i idle 0:07:07 timeout 3:00:00
TCP PAT from inside:192.168.11.9/54558 to outside:192.168.33.76/54558 flags ri idle 0:01:06 timeout 0:00:30
ASA1(config)#
ASA1(config)# sho nat pool
NAT pool outside:obj_192.168.33.70-75_any, range 192.168.33.70-192.168.33.75, allocated 6
TCP PAT pool outside, address 192.168.33.76, range 1-511, allocated 0
TCP PAT pool outside, address 192.168.33.76, range 512-1023, allocated 0
TCP PAT pool outside, address 192.168.33.76, range 1024-65535, allocated 3
It is clear that the ASA is using the fallback IP as the configuration intends it to.
Using the Interface IP for Fallback
In this scenario, the exit interface IP is utilized for PAT services, thereby backing up any NAT pool.
The configuration of the global IP pool is similar to Dynamic NAT without fallback – the object for the global IP pool simply needs a range of IPs in it. The actual fallback is configured on the nat statement. This demonstration will be reusing the obj_192.168.33.70-75_any pool defined earlier. The demonstration will also be performed for both outside and dmz1 interfaces to illustrate key differences.
All previous NAT configuration is removed from the ASA as a first step.
ASA1(config)# clear configure nat
!
ASA1(config)# sho run object id obj_192.168.33.70-75_any
object network obj_192.168.33.70-75_any
range 192.168.33.70 192.168.33.75
!
ASA1(config)# sho run object id obj_192.168.11.0_outside
object network obj_192.168.11.0_outside
subnet 192.168.11.0 255.255.255.0
!
ASA1(config)# sho run object id obj_192.168.11.0_dmz
object network obj_192.168.11.0_dmz
subnet 192.168.11.0 255.255.255.0
Next, NAT statements are configured for both the objects containing internal IPs.
ASA1(config)# object network obj_192.168.11.0_outside
ASA1(config-network-object)# nat (inside,outside) dynamic obj_192.168.33.70-75_any interface
ASA1(config-network-object)# object network obj_192.168.11.0_dmz
ASA1(config-network-object)# nat (inside,dmz1) dynamic obj_192.168.33.70-75_any interface
ASA1(config-network-object)#
For verification, 12 simultaneous connections are launched from R1, 6 to R2 and 6 to R4.
Verification on source
R1#sho tcp brief
TCB Local Address Foreign Address (state)
0CE36EA8 192.168.11.6.36171 192.168.34.4.23 ESTAB
0A3DAB78 192.168.11.3.21409 192.168.23.2.23 ESTAB
0B16DEC8 192.168.11.3.30598 192.168.34.4.23 ESTAB
0B153C50 192.168.11.2.34845 192.168.23.2.23 ESTAB
0B16B380 192.168.11.1.39488 192.168.34.4.23 ESTAB
0B16A6F0 192.168.11.6.50843 192.168.23.2.23 ESTAB
0B085EA0 192.168.11.4.29763 192.168.23.2.23 ESTAB
0BAE66E0 192.168.11.5.41432 192.168.34.4.23 ESTAB
0D16CC48 192.168.11.1.54579 192.168.23.2.23 ESTAB
09F809D8 192.168.11.5.34461 192.168.23.2.23 ESTAB
0CD3A330 192.168.11.2.17600 192.168.34.4.23 ESTAB
0BB17FF0 192.168.11.4.22943 192.168.34.4.23 ESTAB
Verfication on destinations
R2#sho tcp brief
TCB Local Address Foreign Address (state)
0CD2C408 192.168.23.2.23 192.168.33.72.21409 ESTAB
0D309060 192.168.23.2.23 192.168.33.75.29763 ESTAB
09F536E8 192.168.23.2.23 192.168.33.70.34461 ESTAB
0BAEB3D8 192.168.23.2.23 192.168.33.71.50843 ESTAB
0BAEF628 192.168.23.2.23 192.168.33.73.34845 ESTAB
0BAEE998 192.168.23.2.23 192.168.33.74.54579 ESTAB
!
R4#sho tcp brief
TCB Local Address Foreign Address (state)
0D16B9F0 192.168.34.4.23 192.168.33.72.39488 ESTAB
0D2FFB80 192.168.34.4.23 192.168.33.75.41432 ESTAB
0B16B130 192.168.34.4.23 192.168.33.71.17600 ESTAB
0D337100 192.168.34.4.23 192.168.33.70.36171 ESTAB
0CD2C0F8 192.168.34.4.23 192.168.33.74.30598 ESTAB
09F7B1C0 192.168.34.4.23 192.168.33.73.22943 ESTAB
It can be seen that each connection is being translated to a unique global IP address and that the pool of 6 addresses for each interface should have been exhausted. This can be verified further on the ASA
ASA1# sho xlate
12 in use, 12 most used
Flags: D - DNS, e - extended, I - identity, i - dynamic, r - portmap,
s - static, T - twice, N - net-to-net
NAT from inside:192.168.11.5 to dmz1:192.168.33.75 flags i idle 0:03:10 timeout 3:00:00
NAT from inside:192.168.11.5 to outside:192.168.33.70 flags i idle 0:03:46 timeout 3:00:00
NAT from inside:192.168.11.1 to dmz1:192.168.33.72 flags i idle 0:03:25 timeout 3:00:00
NAT from inside:192.168.11.1 to outside:192.168.33.74 flags i idle 0:04:07 timeout 3:00:00
NAT from inside:192.168.11.3 to dmz1:192.168.33.74 flags i idle 0:03:18 timeout 3:00:00
NAT from inside:192.168.11.3 to outside:192.168.33.72 flags i idle 0:03:56 timeout 3:00:00
NAT from inside:192.168.11.6 to dmz1:192.168.33.70 flags i idle 0:03:07 timeout 3:00:00
NAT from inside:192.168.11.6 to outside:192.168.33.71 flags i idle 0:03:42 timeout 3:00:00
NAT from inside:192.168.11.2 to dmz1:192.168.33.71 flags i idle 0:03:21 timeout 3:00:00
NAT from inside:192.168.11.2 to outside:192.168.33.73 flags i idle 0:04:00 timeout 3:00:00
NAT from inside:192.168.11.4 to dmz1:192.168.33.73 flags i idle 0:03:15 timeout 3:00:00
NAT from inside:192.168.11.4 to outside:192.168.33.75 flags i idle 0:03:51 timeout 3:00:00
ASA1#
ASA1# sho nat pool
NAT pool outside:obj_192.168.33.70-75_any, range 192.168.33.70-192.168.33.75, allocated 6
NAT pool dmz1:obj_192.168.33.70-75_any, range 192.168.33.70-192.168.33.75, allocated 6
Now 6 more connections with new, unique source IPs are launched from R1, 3 to R2 and 3 to R4
R1#sho tcp brief
TCB Local Address Foreign Address (state)
0CE36EA8 192.168.11.6.36171 192.168.34.4.23 ESTAB
0A3DAB78 192.168.11.3.21409 192.168.23.2.23 ESTAB
0BB19910 192.168.11.8.11260 192.168.34.4.23 ESTAB
0CE37B38 192.168.11.7.20332 192.168.23.2.23 ESTAB
0B16DEC8 192.168.11.3.30598 192.168.34.4.23 ESTAB
0B153C50 192.168.11.2.34845 192.168.23.2.23 ESTAB
0B16B380 192.168.11.1.39488 192.168.34.4.23 ESTAB
0B16A6F0 192.168.11.6.50843 192.168.23.2.23 ESTAB
0B085EA0 192.168.11.4.29763 192.168.23.2.23 ESTAB
0BAE66E0 192.168.11.5.41432 192.168.34.4.23 ESTAB
0CE387C8 192.168.11.8.40499 192.168.23.2.23 ESTAB
0D16CC48 192.168.11.1.54579 192.168.23.2.23 ESTAB
0CE39458 192.168.11.9.21716 192.168.23.2.23 ESTAB
09F809D8 192.168.11.5.34461 192.168.23.2.23 ESTAB
0BB18C80 192.168.11.7.15290 192.168.34.4.23 ESTAB
0CD3A330 192.168.11.2.17600 192.168.34.4.23 ESTAB
0BB1A5A0 192.168.11.9.32897 192.168.34.4.23 ESTAB
0BB17FF0 192.168.11.4.22943 192.168.34.4.23 ESTAB
R1#
The nature of these new translations and the mapped IP can be verified on the ASA.
ASA1# sho xlate
18 in use, 18 most used
Flags: D - DNS, e - extended, I - identity, i - dynamic, r - portmap,
s - static, T - twice, N - net-to-net
NAT from inside:192.168.11.5 to dmz1:192.168.33.75 flags i idle 0:08:45 timeout 3:00:00
NAT from inside:192.168.11.5 to outside:192.168.33.70 flags i idle 0:09:20 timeout 3:00:00
TCP PAT from inside:192.168.11.7/15290 to dmz1:192.168.34.3/15290 flags ri idle 0:03:43 timeout 0:00:30
TCP PAT from inside:192.168.11.7/20332 to outside:192.168.23.3/20332 flags ri idle 0:04:03 timeout 0:00:30
NAT from inside:192.168.11.1 to dmz1:192.168.33.72 flags i idle 0:08:59 timeout 3:00:00
NAT from inside:192.168.11.1 to outside:192.168.33.74 flags i idle 0:09:41 timeout 3:00:00
NAT from inside:192.168.11.3 to dmz1:192.168.33.74 flags i idle 0:08:53 timeout 3:00:00
NAT from inside:192.168.11.3 to outside:192.168.33.72 flags i idle 0:09:30 timeout 3:00:00
TCP PAT from inside:192.168.11.8/11260 to dmz1:192.168.34.3/11260 flags ri idle 0:03:39 timeout 0:00:30
TCP PAT from inside:192.168.11.8/40499 to outside:192.168.23.3/40499 flags ri idle 0:03:58 timeout 0:00:30
NAT from inside:192.168.11.6 to dmz1:192.168.33.70 flags i idle 0:08:42 timeout 3:00:00
NAT from inside:192.168.11.6 to outside:192.168.33.71 flags i idle 0:09:17 timeout 3:00:00
NAT from inside:192.168.11.2 to dmz1:192.168.33.71 flags i idle 0:08:56 timeout 3:00:00
NAT from inside:192.168.11.2 to outside:192.168.33.73 flags i idle 0:09:34 timeout 3:00:00
NAT from inside:192.168.11.4 to dmz1:192.168.33.73 flags i idle 0:08:50 timeout 3:00:00
NAT from inside:192.168.11.4 to outside:192.168.33.75 flags i idle 0:09:26 timeout 3:00:00
TCP PAT from inside:192.168.11.9/32897 to dmz1:192.168.34.3/32897 flags ri idle 0:01:46 timeout 0:00:30
TCP PAT from inside:192.168.11.9/21716 to outside:192.168.23.3/21716 flags ri idle 0:03:52 timeout 0:00:30
Finally, the creation of the new, on-demand PAT pool can also be verified on the ASA.
ASA1# sho nat pool
NAT pool outside:obj_192.168.33.70-75_any, range 192.168.33.70-192.168.33.75, allocated 6
NAT pool dmz1:obj_192.168.33.70-75_any, range 192.168.33.70-192.168.33.75, allocated 6
TCP PAT pool outside, address 192.168.23.3, range 1-511, allocated 0
TCP PAT pool outside, address 192.168.23.3, range 512-1023, allocated 0
TCP PAT pool outside, address 192.168.23.3, range 1024-65535, allocated 3
TCP PAT pool dmz1, address 192.168.34.3, range 1-511, allocated 0
TCP PAT pool dmz1, address 192.168.34.3, range 512-1023, allocated 0
TCP PAT pool dmz1, address 192.168.34.3, range 1024-65535, allocated 3
For the fallback IP, the ASA creates two distinct PAT pools, one each for the outside and the dmz1 interface, utilizing the respective IPs configured on the interfaces.
Using Manual NAT
The concepts discussed under NON are applicable, as usual, directly under Manual NAT. The blog post will list the syntax for all the examples above using Manual NAT but not the detailed verifications for the sake of brevity.
Caveat – As with all things Manual NAT, the following configuration examples are one possible method of achieving the end result. There are several other configurations that can produce the same result.
The names for the objects are the same as the NON example and the descriptions for the objects can be found in that section.
Configuring a Specific Fallback IP
It should be noted that the configuration is performed only for inside-to-outside translation as it was for the NON example
object network obj_192.168.33.70-75_any
range 192.168.33.70 192.168.33.75
object network obj_192.168.33.76_fallback
host 192.168.33.76
!
object-group network OG_NAT_Fallback
network-object object obj_192.168.33.70-75_any
network-object object obj_192.168.33.76_fallback
!
nat (inside,outside) source dynamic obj_192.168.11.0_outside OG_NAT_Fallback
Using the Interface IP for Fallback
object network obj_192.168.33.50-55
range 192.168.33.50 192.168.33.55
object network obj_192.168.33.60-65
range 192.168.33.60 192.168.33.65
object network obj_192.168.11.0_outside
subnet 192.168.11.0 255.255.255.0
object network obj_192.168.11.0_dmz
subnet 192.168.11.0 255.255.255.0
!
nat (inside,outside) source dynamic obj_192.168.11.0_outside obj_192.168.33.60-65 interface
nat (inside,dmz1) source dynamic obj_192.168.11.0_dmz obj_192.168.33.50-55 interface
