Do you recall when service providers typically had to call upon Remote Trigger Blackhole (RTBH) to mitigate DDOS attacks? With RTBH, we only had two methods, source-based and destination-based. We would basically take the hardest approach. Either drop all traffic from the source or drop all traffic to the destination. This could be both wanted and unwanted traffic.
For those unfamiliar with RTBH, when we say destination-RTBH, we have configured a specific next-hop set to Null0. When a trigger router is initiated, it injects routes to this destination, changing the next hop to the specifically configured next-hop. We can also identify this as the “drop” next-hop.
Comparable to destination-based, source-RTBH utilizes a trigger router to inject routes from the source to drop. The key factor is Unicast Reverse Path Forwarding (uRPF) which is utilized to drop the packets since we set the next-hop to Null0.
What about ACLs? These are still the most widely used mitigation tool for DDoS. Unfortunately, these provide too much overhead and maintenance. ACLs with several hundred ACEs become cumbersome and are hard to define specific lines configured.
It would be great to utilize a mechanism that allows us to be more granular. What if we could create instructions that would match a specific flow based on the following:
- Source
- Destination
- Layer 4
- Packet specific items (length, fragment, e.g)
This is what BGP Flowspec provides: a very granular approach to DDoS mitigation.
Defined in RFC 5575 and updated by the IETF, we now utilize new SAFI Definitions:
- AFI 1 / SAFI 133 – IPv4 dissemination of Flowspec Rules
- AFI 1 / SAFI 134 – VPNv4 dissemination of Flowspec Rules
- AFI 2 / SAFI 133 – IPv6 dissemination of Flowspec Rules
- AFI 2 / SAFI 134 – VPNv6 dissemination of Flowspec Rules
BGP Flowspec matches a particular flow and with this flow, we can effectively install dynamic actions that can either drop traffic, place it into a different forwarding instance for further examination, or police to a desired rate.
Here are a few of the match fields supported by BGP Flowspec:
- Destination Address
- Source Address
- IP Protocol
- Source Port
- Destination Port
- ICMP Code
- TCP Flags
BGP Flowspec defines extended communities as actions to be performed on match fields such as:
- Traffic rates (drop/police)
- Next-Hop Redirect
- VRF Redirect
- DSCP Markings
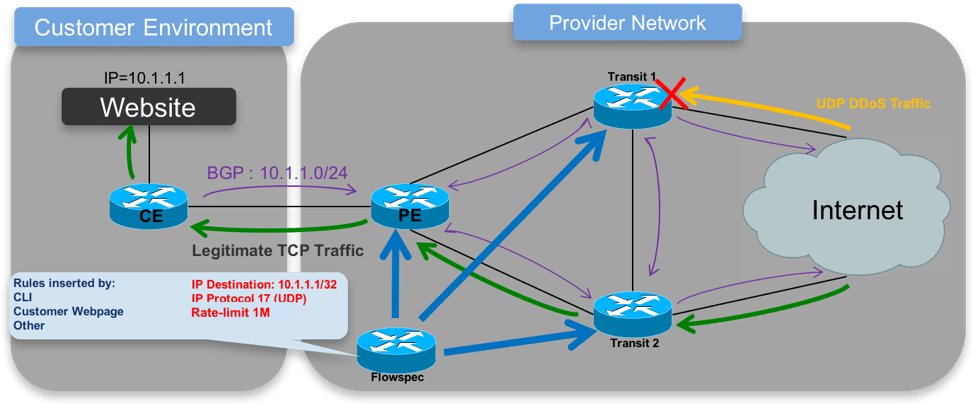
Let’s take a look at an illustration of the BGP Flowspec Architecture:
As we look at this diagram, we must first acknowledge the Flowspec Router. This is the controller that injects the BGP Flowspec NLRIs. The Flowspec router advertises these flows to the other routers in the provider network. Once received, these devices program the flows in hardware and based on the lookup, the devices can take the appropriate action. In this topology, we are going to rate-limit DDoS Traffic to 1M at the Edge.
Overall, there are many ways that BGP Flowspec can help mitigate DDoS attacks within our environments. To take a deeper look into this technology please review my references and helpful links below:
RFC 5575 – Dissemination of Flow Specification Rules
Dissemination of Flow Specification Rules for IPv6
BGP FlowSpec Route-reflector Support
Comments
I look forward to any and all comments regarding this subject. Having performed a proof-of-concept (POC) for this technology, I welcome any design and configuration questions that you may have. We can definitely take a deeper dive into BGP-FS.

BGP FlowSpec + Arbor/Imperva + ExaBGP/NetfastMon = Full of win. We’re almost finishing our solution based on those and having a full night of sleep again is just priceless. 🙂