Gigamon used its #NFD16 presentation time to present, but also had two of its partners do a good bit of the talking. This blog will try to summarize all the good things I heard, but be sure to see the recorded videos for the slides and the details!
Gigamon representatives were kind enough to come talk with me and some other NetCraftsmen a few months back. They distinguished themselves from Ixia by stating that their mission was visibility (Network Packet Broker), while their partners do the processing of the data. That strikes me as a wise choice; you can compete or you can partner , and the ROI on partnering might be a whole lot better. Independent of company size, partnering is how you leverage limited R&D staff resources better.
, and the ROI on partnering might be a whole lot better. Independent of company size, partnering is how you leverage limited R&D staff resources better.
As of NFD16, the Gigamon story has migrated a little away from “we do the visibility (NPB).” Now, Gigamon provides the ASIC and some offload processing, but, yes, still feeds data to partners for analysis. That makes sense: Do the “packet processing edge” functions, and let companies with an existing presence in analysis, security, and other packet visibility post-processing do their thing well.
To misquote Clint Eastwood, “A company’s got to know its limitations.” (Not to imply anything negative; more in the sense of it’s wise to not try to do everything — focus on your strengths.)
Gigamon’s presentation agenda for NFD16:
- Defender Lifecyle Model
- Integration with Splunk
- Amp the Signal, Reduce the Noise
- Gigamon Adaptive Response Application for Splunk
- Integration with Phantom
I’ll summarize each of these.
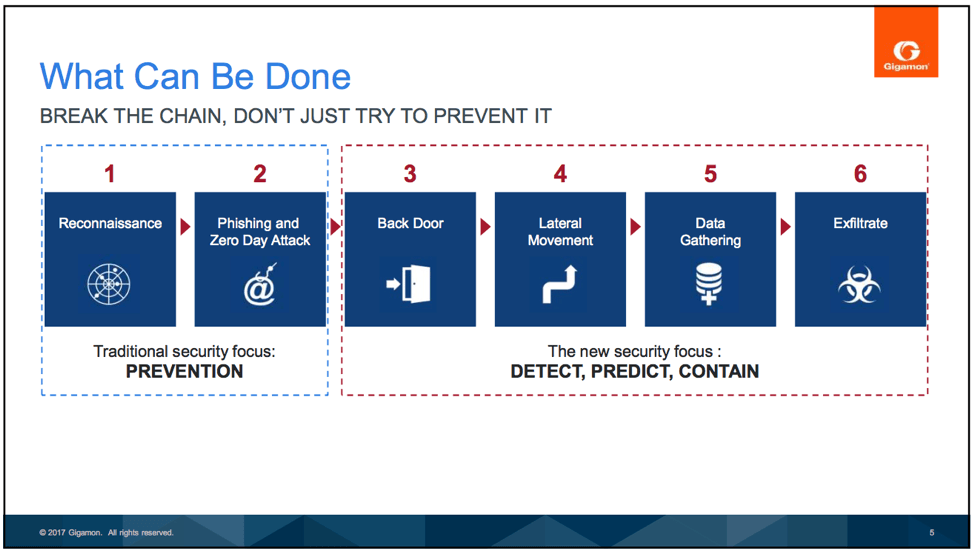
What is the Defender Lifecycle Model?
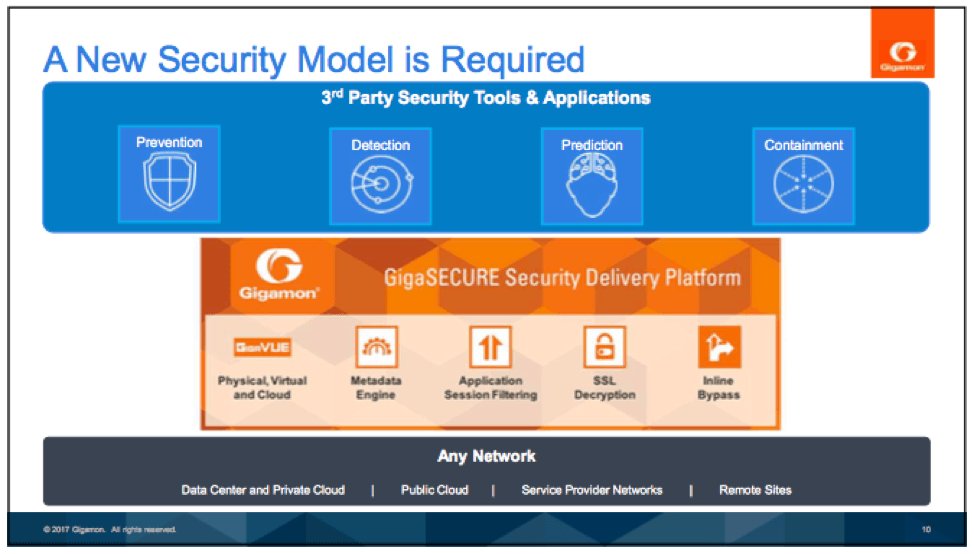
Gigamon has a picture for that:
As a solution, Gigamon touts a Security Delivery Platform, which connects to the physical and virtual networks (cloud!); provides forensic metadata, targeted inspection, and detection of encrypted threats; and feeds partner tools. GigaSECURE is their answer, doing physical/virtual/cloud, metadata engine, application session filtering, SSL decryption, and inline bypass.
The result is shown graphically as:
Part of the intent is faster detection and mitigation.
(Fast forwarding…)
Splunk Integration
Splunk then presented on its growing role via Splunk Enterprise Security, as an “Analytics-driven Next Generation SIEM,” and its role as “Industry Leading Platform for Machine Data,” able to process multiple forms of data. In particular, Splunk highlighted Adaptive Response (AR). The idea: Dealing with complexity, plus achieving faster time to respond, requires automation, analytics-driven decisions, and passing that to Adaptive Response. Splunk has Adaptive Response partners to handle process information or grant/revoke access, change firewall rules, etc.
Part of the message was that Gigamon metadata can help provide Splunk (and security personnel) with the information to make better decisions.
Amp the Signal, Reduce the Noise
Gigamon then presented on its metadata capabilities, which they claim help the SIEM avoid being overwhelmed with data — e.g. IPFIX data, HTTP return codes, questionable domains via Shannon entropy, etc. (See the video for more details.)
Gigamon Adaptive Response Application for Splunk
This is Gigamon coding that leverages the Splunk AR framework, and which can bind actions to pre-defined or user searches in Splunk, triggering automated or ad hoc actions from Splunk Enterprise Security.
Phantom Integration
Phantom provides Security Automation and Orchestration. That’s the tail end of the security response chain: doing something about a threat! Their product centers on orchestrating and integrating the use of various security tools — see the video segment for logos. The tools can investigate, or they can react.
Gigamon has an app for that: They can send a subset of traffic to a tool for investigation, or block some subset of traffic. This is done via four basic actions: post or delete a rule, and get map or get maps.
For the demo, see the videos.
Related Articles
- NFD16 – Gigamon and Splunk (with a Dash of Phantom)
- Gigamon Remakes Itself for Cloud
- Personal Transformation (Ethan Banks compares Gigamon cloud transformation to personal job skills changes)
- SSL Decryption for Increased Network Visibility
Comments
Comments are welcome, both in agreement or constructive disagreement about the above. I enjoy hearing from readers and carrying on deeper discussion via comments. Thanks in advance!