This is one of several blogs about the vendor presentations during Network Field Day 19, which took place November 7-9, 2018. This blog contains a summary of the vendor presentations and (of course) my comments or opinions (I’ll share at least some of them).
If this blog motivates you to greater interest in what the vendor had to say, you can find the cleaned up streaming video of their presentations at the Tech Field Day YouTube channel, specifically the NFD19 playlist, or by clicking on the vendor’s logo on the main #NFD19 web page (linked above).
About Illumio
Let’s talk about Illumio. Illumio perhaps had the best demos of NFD19, and maybe even the best ever!
Presentation by Matt Glenn, Vice President of Product Management, Illumio
Let’s go over the basics of what Illumio does, and then a bit about the demos. So, what does the Illumio product do?
Illumio’s Adaptive Security Platform (ASP) provides a rather different approach to micro-segmentation. ASP does enforcement via a Virtual Enforcement Node (VEN) agent at the workload level, providing host / process, VM, or container-based micro-segmentation and traffic visibility. Each agent acts as a sensor, tracking various KPIs including packets / flows.
The flows are collected by the Policy Compute Engine (PCE). The GUI provides application dependency mapping (ADM) and a multi-level zoomable diagram. You can then use the GUI to create application groups (e.g. web / app / DB tiers, or groupings of micro-services), propose a security policy for them based on observed flows. You may then edit and test or enforce the policy. When you do that, the PCE instantiates the policy in the endpoints.
From their web page, Illumio can also automate ACLs in load balancers and switches, but the #NFD19 presentations and demos didn’t go into that.
The centralized policies built in the ASP Policy Compute Engine (PCE) use labels rather than IP addresses. It is up to you to assign the labels to nodes.
In test mode, the deployed policy in effect ends with “permit any any log” and alerts you to any observed traffic that did not match an ACL rule. You then let the policy “cook” for some period of time to catch quarterly or annual-only application traffic flows, if you so wish. Enforce mode can also alert you to blocked flows.
The actual PCE is typically a cluster of VM’s.
Announced / New!
Illumio announced that they now support a PCE SuperCluster. I’d say, “cluster cluster”, but that might give the wrong idea. Think hierarchical clustering. The idea is to replicate policy between regional PCE clusters to support a global, highly scalable, and highly available policy control mechanism.
Illumio also does vulnerability mapping, ID’ing vulnerabilities on the various workloads. This allows automated mitigation (after review / approval) to block inbound traffic to exploitable ports. Illumio obtains and integrates the vulnerability data for you.
Those Amazing Demos
Illumio spent most of their NFD19 session demonstrating. And what impressive demos!
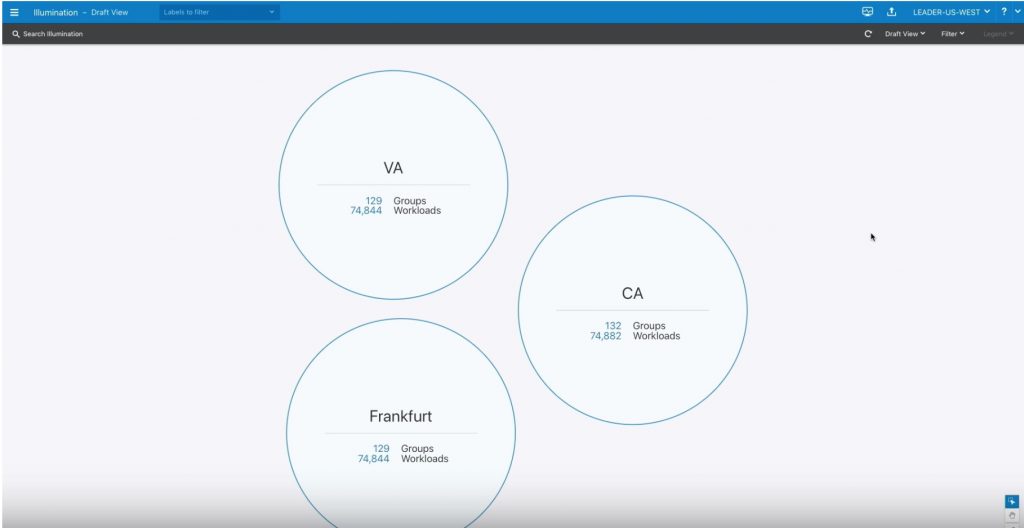
Illumio had set up 3 regions as literal AWS regions (Virginia, California, Frankfurt), with 75,000 simulated workloads (OS instances) in each. A workload is bare metal, VM, or container. The SuperCluster then managed all of that.
The demos covered:
- Global Visibility
- Global Policy Portability
- Intra Region Resiliency
- PCE Disaster Recovery
- Vulnerability-Based Segmentation
I’ll refer you to the videos for the details.
Teaser: if you pay close attention, you can see that the presenter, Matt Glenn, introduced each new topic by pulling on a new T-shirt over the existing shirt stack. That made it all hot stuff (at least for Matt)!
Conclusion
This is pretty cool stuff. It is automated leveraging of endpoints, rather than dedicated firewalls, to provide uniform micro-segmentation onsite or in the cloud. The focus is on the segmentation and policy, i.e. omits the connectivity and automation aspects of Cisco ACI and VMware. Put differently: platform vendor neutral.
Comments
Comments are welcome, both in agreement or constructive disagreement about the above. I enjoy hearing from readers and carrying on deeper discussion via comments. Thanks in advance!
—————-
Hashtags: #CiscoChampion #TheNetCraftsmenWay #Illumio #NFD19 #MicroSegmentation
Twitter: @pjwelcher
NetCraftsmen Services
Did you know that NetCraftsmen does network /datacenter / security / collaboration design / design review? Or that we have deep UC&C experts on staff, including @ucguerilla? For more information, contact us at info@ncm2020.ainsleystaging.com.