This is one of several blogs about the vendor presentations during Network Field Day 19, which took place November 7-9, 2018. This blog contains a summary of the vendor presentation and any related comments or opinions I might have (I’ll share at least some of them).
If this blog motivates you to greater interest in what the vendor had to say, you can find the cleaned up streaming video of their presentations at the Tech Field Day YouTube channel, specifically the NFD19 playlist, or by clicking on the vendor’s logo on the main #NFD19 web page (linked above).
Kentik at #NFD19
Kentik presented about their cloud-based big data approach to analyze many kinds of flow data, both from internal sources and cloud sources. Kentik goes beyond many NetFlow tools by ingesting cloud flow logs and other types of information, automating detection of supporting information (BGP, geo-location, etc.) and innovating to add business and technical value to reports. Kentik Detect also provides threshold and anomaly alerting. And of course, flow data now has a security role as well.
Avi Freedman (Co-founder and CEO) presented on “Tagging and Enrichment”. I have my own personal spin on this. I think most of us that have worked with NetFlow tools feel like we exhausted their possibilities pretty quickly: packets, source IP, destination IP, protocol, port, etc. There’s also some pain associated with having to interpret the raw data.
Kentik goes beyond that limiting perspective. One of Avi’s / Kentik’s key insights is that if you add contextual information to the flow data, you enhance its reporting and make it more business relevant and easier to consume the data. I.e. making the data useful to the business, without working at the packet-level.
For example, pulling up data by site name rather than IP, ports as named applications, etc. Tie in BGP data so you can identify network exit points (important for Service Providers / large WAN cost management). Tie in SNMP data to get interface names.
Jim Meehan (Director of Product Marketing) covered some of this in his Service Provider presentation. Interesting capabilities include My Kentik white-label portals for customer-specific views of data.
Business relevance means that Kentik moves beyond IT, for instance it can help sales prospecting in Service Providers.
Kentik can use its k-probe agent to get better data from servers. Avi noted that they’re now having to show value in order to get the agent onto servers. Thinking as a server owner might: time / hassle, need to support agent going forward, potential performance impact or interaction with other agents, risk, etc. I hear that adding flow / packet agents or security agents or APM agents is tough to accomplish!
Avi also mentioned that Kentik is seeing more automation / workflow integration, including ServiceNow.
The most recent feature from Kentik is the ability to ingest AWS and Google flow records. Azure is apparently coming in 2019.
The final demo by Jim really caught my eye. You can findit after Crystal Li’s presentation on leveraging cloud information.
For that demo, the group was invited to connect to http://sockshop.gcp.kentik.io and drive the (simple) container-based website to generate traffic between components. Jim then showed the ensuing GCP flow information and some report she’d set up. Jim had added Istio service mesh to the setup, to get latency data by URL path, without having to add agents.
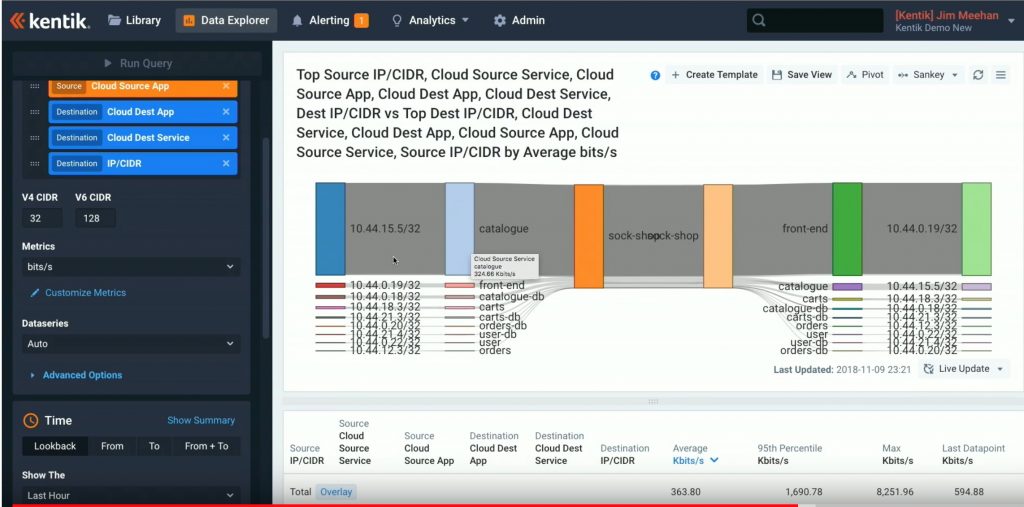
This is a cool capability: network type data for VM or container flows, and not having to get app owners to install agents. Also, reporting not tied to a particular toolor cloud (admittedly limited by whatever the cloud provider does export).
I’m sure the various forms of flow data will have their strengths, weaknesses, and just plain gaps.
I highly recommend you watch Avi’s tech talk and the Cloud demo. The closing “What’s Next” section might also be of interest. The #NFD19 delegates really liked the negative roadmap discussion.
Comments
Comments are welcome, both in agreement or constructive disagreement about the above. I enjoy hearing from readers and carrying on deeper discussion via comments. Thanks in advance!
—————-
Hashtags: #CiscoChampion #TheNetCraftsmenWay #Kentik #NFD19 #Cloud #BigData
Twitter: @pjwelcher
NetCraftsmen Services
Did you know that NetCraftsmen does network /datacenter / security / collaboration design / design review? Or that we have deep UC&C experts on staff, including @ucguerilla? For more information, contact us at info@ncm2020.ainsleystaging.com.


